Types of two-factor authentication: pros and cons
The development of modern technologies and the transition of business to an online environment has led to the emergence of new fraudulent schemes aimed at stealing personal data. So, in response to the increased level of various cyber threats, more and more services and companies are beginning to implement Two-Factor Authentication (2FA) into their operations.
The multi-factor authentication market (MFA) has been constantly increasing over the past years. In 2022, the global MFA was estimated at nearly 13 billion U.S. dollars, and was forecast to double its value by 2027.
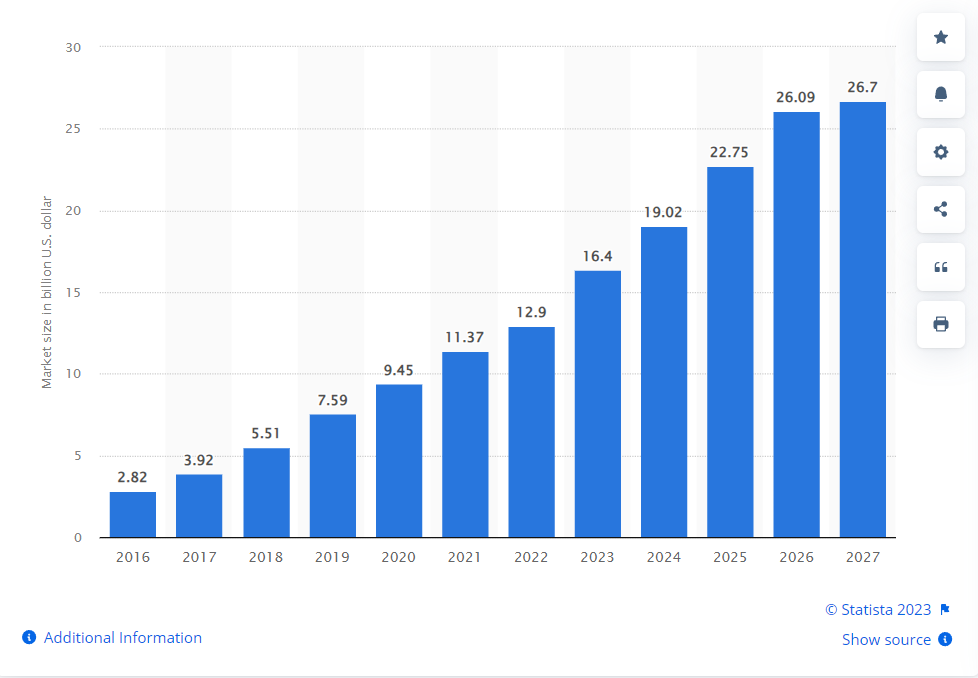
Multi-factor authentication (MFA) market size worldwide from 2016 to 2021 with a forecast from 2022 to 2027.
What is 2FA authorization?
This is a type of multi-factor authentication, which requires two different forms of identity verification from the customer in order to access a personal account. For example, to gain access to your bank's application, you need to undergo two-factor authentication, which usually involves entering your username and password, as well as a verification code received via SMS.
What is authentication?
The term means the procedure of providing information that is required by the system from the user in the process of logging in to the account. That is, by correctly providing self-identification data, a person can confirm that he or she is who he or she claims to be.
At the moment, authentication is one of the most common cybersecurity practices that significantly reduces the risk of cybercrimes.
What is an authentication factor?
During the authentication process, the individual must provide a certain type of information, each of which is called an authentication factor. To pass 2FA Authorization, the user must enter data from two different factors. Here are the main ones:
Biometric data
This type is based on the provision of a person's physical characteristics. For example, it may include passing a face-ID or fingerprint scanne
Pros:
- Difficult to forge or replicate.
- Convenient for users.
Cons:
- Biometric data can be compromised.
- Implementation costs and potential privacy concerns.
Knowledge
The essence of this factor is to give personal information that only the user can know. It may be answers to security questions, as well as knowledge of passwords and so on.
Pros:
- Familiar and easy to use.
- No need for additional hardware.
Cons:
- Vulnerable to phishing attacks if users unknowingly provide information.
Possessions
In this category is included the possession of any physical objects that can help in the authentication procedure. The most common example is having a mobile phone that can receive text messages with a confirmation code for logging in or that can be called to verify identity.
Pros:
- Adds an extra layer of security.
- Often involves a physical token or device.
Cons:
- Users may lose the physical token.
- Some methods, like SMS, are susceptible to SIM swapping attacks.
Geographic location
Tools (e.g. GPS-based) that can determine the location of the person trying to access the account are included in this factor. If the location is not the same as usual, the sign-in will fail.
Pros:
- Adding geographic location as a factor provides an additional layer of security, as it ensures that the user is attempting to access the account from an expected and authorized location.
- Helps to prevent unauthorized access from distant or unusual locations, which can be a sign of a compromised account.
- When combined with other 2FA methods, geographic location verification adds an extra dimension to the authentication process, making it more robust.
Cons:
- Users may encounter difficulties if they are legitimately trying to access their accounts from a new or unexpected location, leading to false negatives and potential account lockouts.
- The accuracy of geographic location tools, especially those relying on GPS, can be affected by factors like poor signal strength, weather conditions, or device limitations, potentially leading to authentication errors.
- Location-based authentication raises privacy concerns, as it involves tracking and storing the geographic data of users. Striking the right balance between security and privacy is crucial.
Reasons to use 2FA
The prevalence of cybercrimes is truly impressive. That's why a lot of people are abandoning single-factor authentication in favor of 2FA, because even if someone gets the password to account, there's another major obstacle in the form of identity verification. This option can increase the security of your personal data and help you avoid the risks of phishing.
Also, it's worth mentioning that if you're a business owner, two-factor authentication may be required from you by law. This is especially true if you work with the sensitive date of your customers.
Read also: Key Steps to Improve Cybersecurity in Healthcare
Drawbacks you may encounter
Like any other technology, two-factor authentication of course has its drawbacks too.
For customers:
- There is no way to afford two-factor authentication. The most common reason for this can be the lack of a modern phone or any other gadget that would support such a feature.
- Problems due to loss of access to one of the authentication factors. This can make it difficult to access a personal account and take some time to solve it.
For companies:
- Additional costs. Of course, implementing and maintaining 2FA requires considerable expenses. That is why, not every company can afford to use such technology, although it certainly brings a lot of advantages to the company as a whole.
Read also:
Requirements for Cybersecurity Ensuring of Healthcare IoT Systems
Best Practices of Security & Protection of Mobile Applications
IT outsourcing with SDH
Implementing technological solutions into your business model that will improve its efficiency and productivity is not an easy process that is often out of the hands of your in-house workers. Software Development Hub is ready to provide you with a dedicated team of experts who can handle it.
Our experts are ready to take care of all stages of software development, from planning to technical support of the finished solution. Also, at each stage of work we maintain close communication with you, take into account your opinion and wishes, as well as report on the progress of work, so that you can be sure that you will get the desired result within the specified timeframe.
In order to get a consultation about your project with us as soon as possible — fill out a special form and our experts will contact you!
Categories
Share
Need a project estimate?
Drop us a line, and we provide you with a qualified consultation.