Requirements for Cybersecurity Ensuring of Healthcare IoT Systems
Healthcare IoT systems are introducing promising solutions into daily life. This reduces operational costs, increases the popularity of such healthcare services among patients, the speed of computing and ease of access to such services, the optimal use of resources, the sharing of records, and the support of scientific research, etc. On the other hand, such systems are facing the problem of security in general, which may also include data protection and cybersecurity.
Such systems also include patients’ end devices, healthcare organizations, and doctors (Fig. 1). In most cases, their interaction requires permanent wireless communication, which is necessary to get and send data.
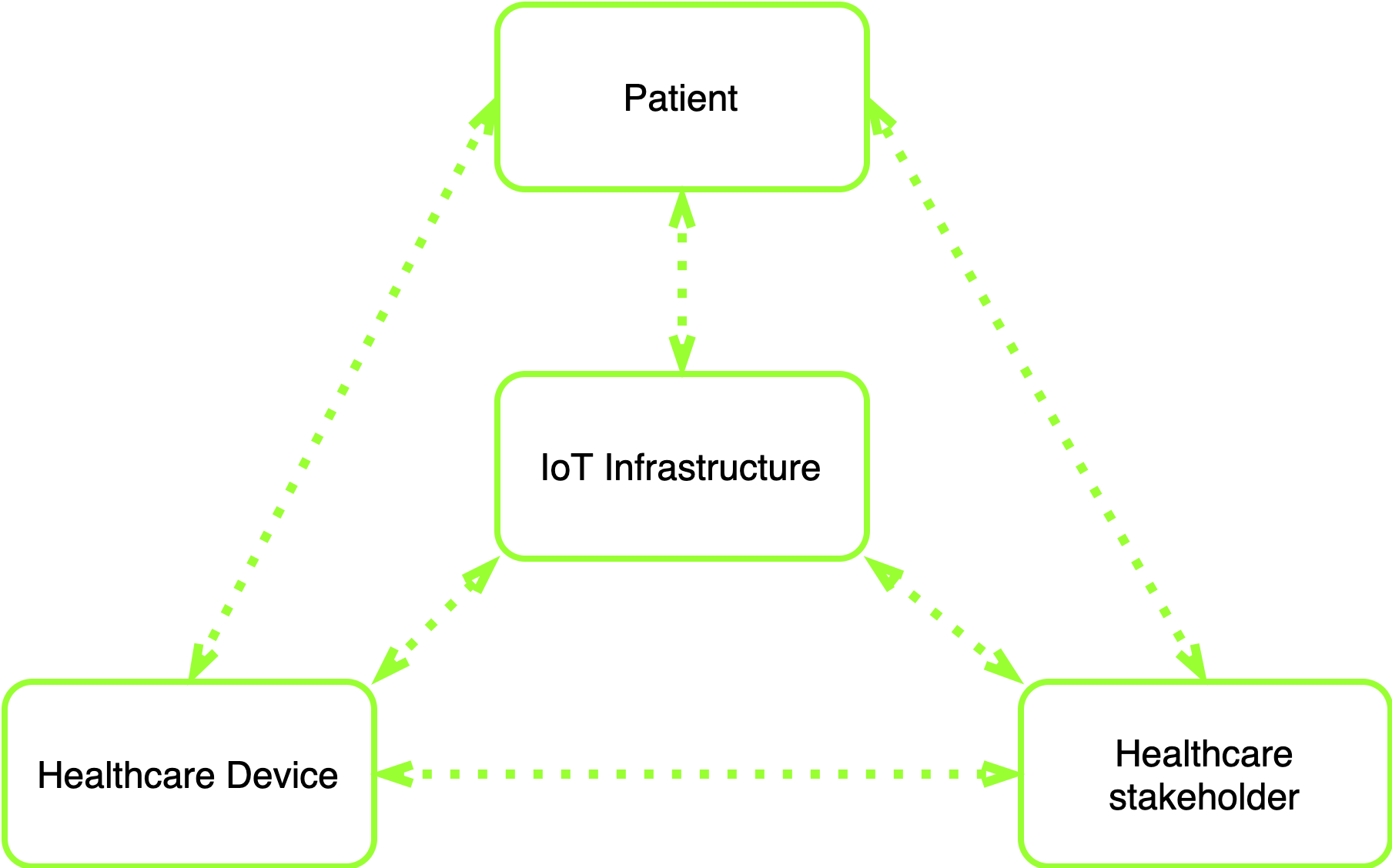
Fig. 1 — Interaction between main components of healthcare IoT systems
In general, the process of such systems functioning in terms of cybersecurity is shown in Fig. 2.
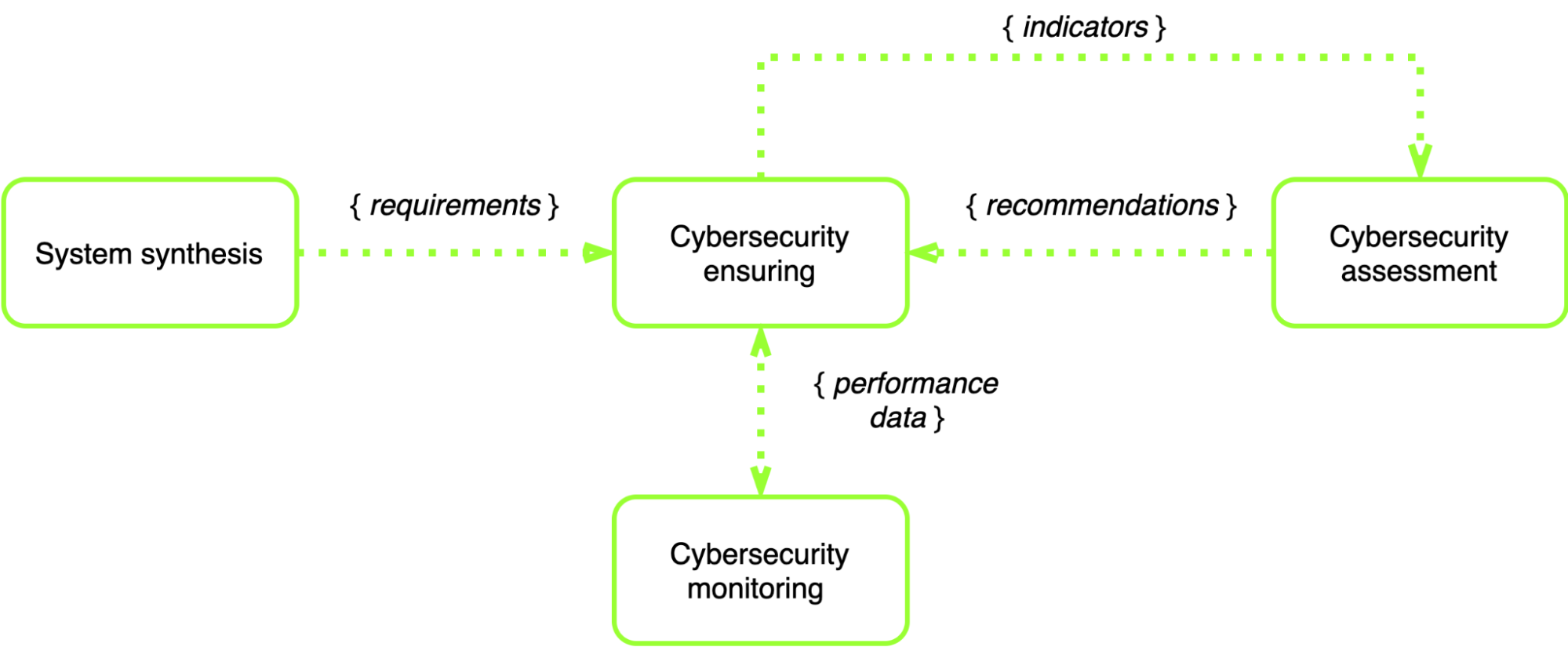
Fig. 2 — Cybersecurity functioning process of healthcare IoT systems
According to this process, the synthesis and analysis of the healthcare IoT system that needs to be developed, is being developed, or has already been developed and is currently maintained by the support, are taking place to elicit the requirements for cybersecurity. To ensure cybersecurity, it is necessary to constantly monitor and assess the current state with the help of special technical tools.
It is important to emphasize that the permanent assessment of cybersecurity's current state allows to ensure a high level of functioning and prevent errors in the specification of healthcare IoT systems at the early stages of the life cycle.
Analysis of existing international regulatory documents
The requirements and standards of healthcare IoT systems functioning and end-user’s medical devices are mostly regulated by the federal laws of the USA and the Food and Drug Administration (FDA), on the basis of which national standards of other countries have been developed. It should also be noted that such systems include not only software and hardware, but also people, processes and organizational policies (Fig. 3), that is, all levels of requirements should be taken into account.
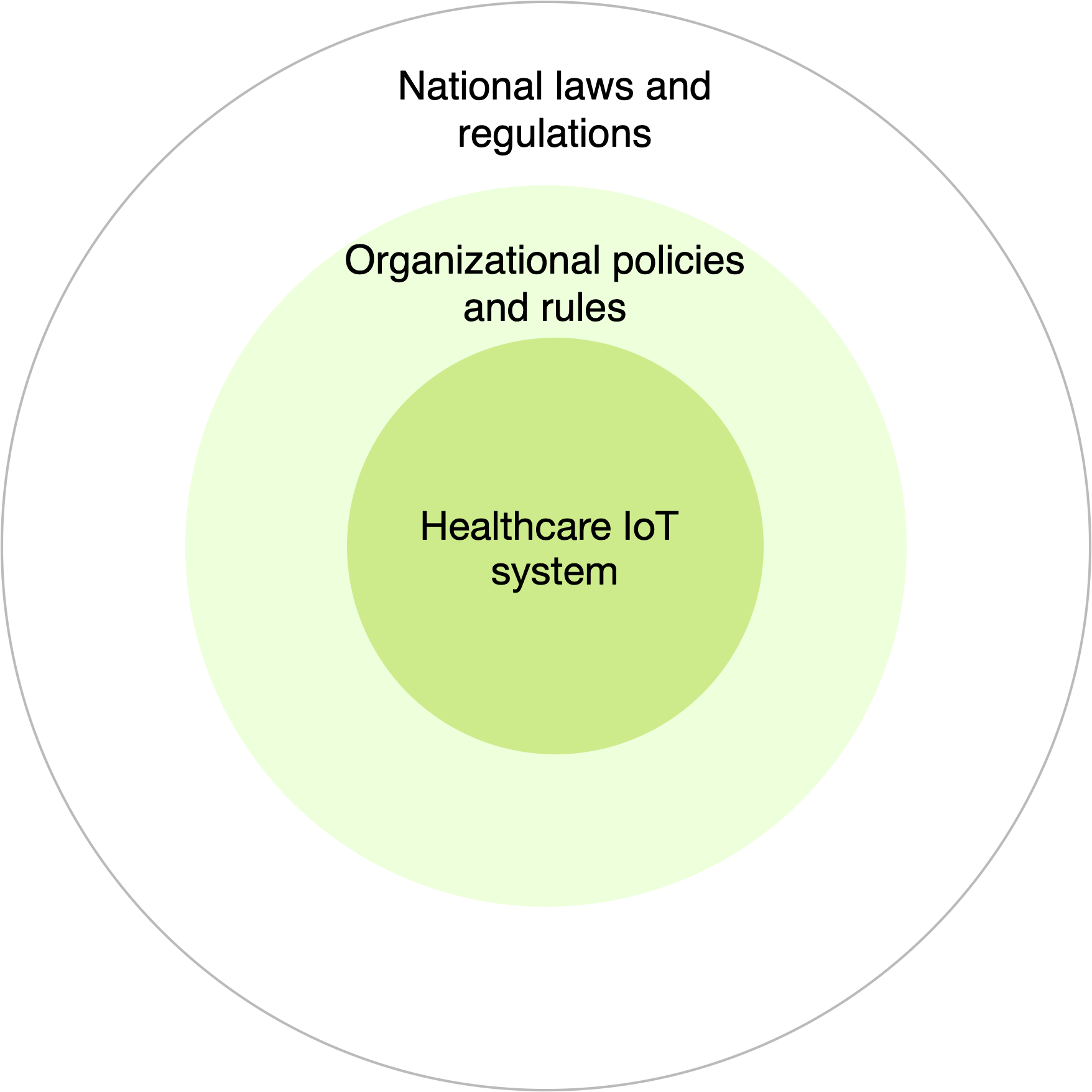
Fig. 3 — A multi-layered structure for determining the sources of requirements for healthcare IoT systems
There are several international standards for the certification of healthcare systems, among which there are those that regulate issues of cybersecurity and other types of security, for example, ISO/IEC 27032:2012, IEC 62304:2006, ISO 82304:2016.
An explanation of the US federal law "Health Insurance Portability and Accountability Act" is the rules of privacy and security. The purpose of this document is to protect the personal data of patients, prohibit the disclosure of medical secrets and punish the guilty in case of violation of certain rules.
The Center for Devices and Radiological Health (CDHR), a division of the FDA, is responsible for premarket approval of all medical devices, as well as overseeing the manufacture, performance, and safety of these devices. It requires healthcare systems device manufacturers to ensure the safety of their products both at the development stage and during the entire service life of these devices.
In the document "Premarket Submissions for Management of Cybersecurity in Medical Devices", the FDA recommends healthcare systems manufacturers develop a set of management documents to reduce the probability of functional capabilities being compromised through inadequate security to maintain the integrity and functionality of healthcare devices. At the same time, the FDA suggests that manufacturers of healthcare systems constantly perform:
- identification of assets, threats, and vulnerabilities;
- assessment of threats and vulnerabilities impact;
- assessment of the threats and vulnerabilities probability;
- determination of risks levels and possible strategies for reducing the impact;
- evaluation of the determination risk and risk acceptance criteria.
The document "Postmarket Management of Cybersecurity in Medical Devices" recommends continuing all the above-mentioned procedures after the product is released to the market. The FDA also recommends manufacturers the NIST Framework for Risk Management using, as well as cybersecurity vulnerability discovery tools to assess factors such as attack vector, attack complexity, required privileges, user interaction, scale, privacy impact, integrity impact, impact on availability, level of corrections, trust, confidence in the report.
In addition, the FDA recommends healthcare systems manufacturers to develop comprehensive risk management programs to ensure cybersecurity, instead of being reactive and fixing system flaws only after they have caused damage.
Determination of requirements for ensuring cybersecurity of healthcare IoT systems
It is necessary to take into account the requirements for each level of the infrastructure of the healthcare IoT system. The table below shows a model of the profile-forming normative base of requirements for each level of such systems of infrastructure is presented.
|
Level |
Standard/Regulatory document |
Context of requirements |
|
Sensors |
NIST Сybersecurity for IoT programs |
Development and implementation of different types of regulations to improve the security of devices and IoT infrastructure, that promotes trust and creates an environment for innovations |
|
ISO/IEC 17789:2014 |
Reference architecture of cloud computing, that includes roles, activities, elements and connections between them |
|
|
IEEE 802.15.4 |
Physical layer and access control for low-frequency wireless personal networks |
|
|
Network |
ISO 27033 |
Securing a network that includes devices, protecting management activities related to devices, applications/services, and end users |
|
NIST 800-53 |
Assessment procedures |
|
|
Service |
FIPS 140-2 |
Cloud and service configurations for static data |
|
ISO 27018 |
Data protection in the cloud, which ensures a systematic approach to data protection and that the provider is a "conscious citizen" in the cloud |
|
|
Health Level 7 |
Transfer of healthcare data between software applications and providers |
|
|
Management |
ISO 27017 |
Security management of cloud computing |
|
Health Information Technology for Economic and Clinical Health, HITECH |
Quality, security and efficiency of the healthcare sector |
|
|
ISO 9001 |
Quality management |
|
|
Risk assessment |
ISO/IEC 9126 |
Product quality assessment |
|
ISO 14971 |
Application of risk management to medical devices |
|
|
Healthcare Information and Management Systems Society, HIMSS |
Compliance with society's requirements for information and management healthcare systems |
|
|
Personal healthcare data protection |
The HIPAA Privacy Rule |
Personal information protection used by healthcare organizations, and provides to patients a set of rights regarding that information and permits the disclosure of personal health information for certain purposes. |
|
“Minimum Necessary” Rule |
The system shall make every reasonable effort to use, request or disclose only the minimum amount of information necessary to achieve its intended purpose |
|
|
The HIPAA Security Rule |
Administrative, physical, and technical measures that healthcare organizations must implement to ensure the confidentiality, integrity, and availability of protected health information |
In summarizing, in general, the main requirements for the cybersecurity of healthcare IoT systems are:
- Ensure that the organization that uses such systems complies with the rules of ensuring cybersecurity. It is strongly recommended to verify existing systems following official regulations.
- Implement a trusted network architecture. It is necessary to avoid vulnerable attacks during the transfer of data from one device to another to ensure the integrity and availability of data.
- Ensure protection of personal healthcare data. It is necessary to ensure the confidentiality of the private data of patients.
References
- Information technology – Security techniques – Guidelines for cybersecurity, ISO/IEC 27032:2012, Brussels: European Committee for Electrotechnical Standardization.
- Medical device software – Software life cycle processes, ISO/IEC 62304:2006, Brussels: European Committee for Electrotechnical Standardization.
- Health software – Part 1: General requirements for product safety, ISO/IEC 62304-1:2006, Brussels: European Committee for Electrotechnical Standardization.
- “The HIPAA Privacy Rule”.
- “The Security Rule”.
- «Helsi – The questions about reform».
- U.S. Department of Health and Human Services, Food and Drug Administration and Center for Devices and Radiological Health. Guidance for Industry – Cybersecurity for Networked Medical Devices Containing Off-the-Shelf (OTS) Software.
- U.S. Department of Health and Human Services, Food and Drug Administration and Center for Devices and Radiological Health. Content of Premarket Submissions for Management of Cybersecurity in Medical Devices.
- U.S. Department of Health and Human Services, Food and Drug Administration and Center for Devices and Radiological Health. Postmarket Management of Cybersecurity in Medical Devices.
- A. Strielkina, O. Illiashenko, M. Zhydenko and D. Uzun, "Cybersecurity of healthcare IoT-based systems: Regulation and case-oriented assessment", 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), pp. 67-73, 2018. DOI: 10.1109/dessert.2018.8409101.
- NIST Сybersecurity for IoT programs.
- Information technology – Cloud computing – Reference architecture, ISO/IEC 17789:2014. Brussels: European Committee for Electrotechnical Standardization.
- IEEE802.15.4 Low-Rate Wireless Personal Area Networks. US, IEEE standards association.
- ISO/IEC 27033-1:2015 Preview Information technology – Security techniques – Network security. Geneva, The international organization of standardization.
- "Security and privacy controls for federal information systems and organizations", NIST Special Publication, rev. 4, pp. 53, 2015.
- “140-2: Security requirements for cryptographic modules,” Information Technology Laboratory, National Institute of Standards and Technology.
- ISO/ IEC 27018:2014(E). Protection for personally identifiable information, Brussels: European Committee for Electrotechnical Standardization.
- Health Level Seven. http://www.hl7.org.
- ISO/IEC 27017:2015. Code of practice for information security controls based on ISO/IEC 27002 for cloud services. Geneva, The international organization of standardization.
- The Health Information Technology for Economic and Clinical Health Act (HITECH) Act.
- ISO 9001:2015. Quality management systems – Requirements. Geneva, The international organization of standardization.
- ISO/IEC 9126:2001. Software engineering – Product quality. The international organization of standardization.
- Medical devices – Application of risk management to medical devices, ISO/IEC 14971, Brussels: European Committee for Electrotechnical Standardization.
- The Healthcare Information and Management Systems Society. http://www.himss.org.
- "HIPAA Privacy Rules for the Protection of Health and Mental Health Information".
Categories
About the author
Share
Need a project estimate?
Drop us a line, and we provide you with a qualified consultation.







